I swear Sty I'm the only guy in the office that wouldn't open a dodgy link... And then they call for me of course when shit hits the fan...Yeah, it's a very common technique that hackers use. It's also usually the way pentests are done.
I once talked with a cybersec expert, who told a story about how he managed to complete a pentest in the time it took the manager to explain what was expected of him, simply because all 4 USB sticks that he dropped were used.
Same with "secured" office files. If you receive a file, Windows Office always open it in "protected mode", which you can then re-open in "edit mode". A common hacking method is to "lock" the file, showing only a large square, with the request to enable edit mode to access the rest of the file. But, it's likely a macro that executes the virus as soon as you open it in edit mode.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Technology: General Discussion
- Thread starter Mave
- Start date
Stybar
Yeah, groupsex seems to be the way to go
- Messages
- 15,798
I must admit, I fell for a phishing attack recently as well (In my defence, it looked pretty legit). Luckily it was a test that was being run by our cybersec department, but still.I swear Sty I'm the only guy in the office that wouldn't open a dodgy link... And then they call for me of course when shit hits the fan...
A good phishing mail is hard to spot, unless you know what to look for. And even then it usually comes down to just dodgy links, and I can understand if a tired mind misreads one of those.
Well shit, it's still there and is annoying as fuck.Just spotted a pixel stuck on red on my LG oled TV... running pixel refresh and praying it’ll be fine in an hour.
FORTUNATELY LG's service is pretty damn good. I just called them and they will have a repair company contact me. The screen will most likely be replaced at no cost.
Stybar
Yeah, groupsex seems to be the way to go
- Messages
- 15,798
But! How long will it take? My guess is that in these times, a repair service will not be eager to go to random people's houses...Well shit, it's still there and is annoying as fuck.
FORTUNATELY LG's service is pretty damn good. I just called them and they will have a repair company contact me. The screen will most likely be replaced at no cost.
Appointment booked for next Wednesday surprisingly. Hopefully the guy will be able to fix it then and there.But! How long will it take? My guess is that in these times, a repair service will not be eager to go to random people's houses...
Fingers crossed!I mean, I hope so, but I don't expect so. If it's a broken pixel, it's likely he'll either have to swap out some circuitboards, or something similar.
I think I might just have bought a steal...
I bought a 16TB drive (needed because largest 8TB drive right now is full) for only €220.
This is the model I bought: https://www.amazon.nl/dp/B00XI36IFC
Take a look at the price:
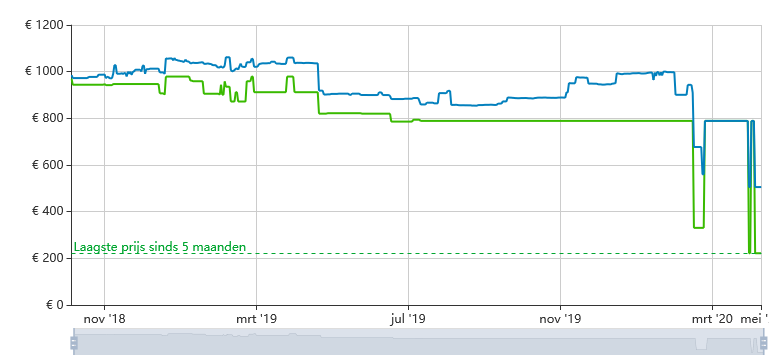
It's also still €800 in other stores..
Hopefully I did a really good deal here.
I bought a 16TB drive (needed because largest 8TB drive right now is full) for only €220.
This is the model I bought: https://www.amazon.nl/dp/B00XI36IFC
Take a look at the price:

It's also still €800 in other stores..
Hopefully I did a really good deal here.
Yeah, don' think so either.I mean, that does seem like a great deal. I don't think it'll drop much lower.
Also they just fixed my TV for free! I got an entire new screen lol. Only the motherboard and other electronic stuff is from the "old TV".
The exact same product is 10 times as expensive on Amazon.com, I'm guessing they forgot a zero 
https://www.amazon.nl/G-RAID-met-verwijderbare-Thunderbolt-USB/dp/B01LVZ2OBC

https://www.amazon.nl/dp/B00XI36IFC/ref=pe_19967891_404437601_TE_item_image?th=1


https://www.amazon.nl/G-RAID-met-verwijderbare-Thunderbolt-USB/dp/B01LVZ2OBC

https://www.amazon.nl/dp/B00XI36IFC/ref=pe_19967891_404437601_TE_item_image?th=1

Stybar
Yeah, groupsex seems to be the way to go
- Messages
- 15,798
And thanks to that, I ended up looking through Amazon's recommended... And managed to snag a new Samsung 860 2TB internal SSD for €200!
My current drive is 500GB, which is fine, but I can't really have more than 2 or 3 games installed... So, an upgrade is more than welcome. And since we're stuck at home, my expenditures have been drastically lower, while my income remains stable, so I had some excess money anyway.
My current drive is 500GB, which is fine, but I can't really have more than 2 or 3 games installed... So, an upgrade is more than welcome. And since we're stuck at home, my expenditures have been drastically lower, while my income remains stable, so I had some excess money anyway.
Nice! I feel you a bit. My C drive is still only 128GB (I need to move and delete stuff constantly), I need to switch it asap with an extra 1TB 970+ I have laying around. (it's in my old laptop)And thanks to that, I ended up looking through Amazon's recommended... And managed to snag a new Samsung 860 2TB internal SSD for €200!
My current drive is 500GB, which is fine, but I can't really have more than 2 or 3 games installed... So, an upgrade is more than welcome. And since we're stuck at home, my expenditures have been drastically lower, while my income remains stable, so I had some excess money anyway.
And I'm going to reinstall my OS right now. Hopefully everything goes smoothly.Nice! I feel you a bit. My C drive is still only 128GB (I need to move and delete stuff constantly), I need to switch it asap with an extra 1TB 970+ I have laying around. (it's in my old laptop)
I think I might just have bought a steal...
I bought a 16TB drive (needed because largest 8TB drive right now is full) for only €220.
This is the model I bought: https://www.amazon.nl/dp/B00XI36IFC
Take a look at the price:

It's also still €800 in other stores..
Hopefully I did a really good deal here.
About that... Amazon just emailed me about a "pricing error", and that my order has been canceled.
Had to wait two weeks only to hear that message. Oh well, when it sounds too good to be true..
I got price alerts on 5 different HDDs now, will have to buy one asap since I have more data backed up in the cloud than in cold storage now.
Ditto. If Google deletes my account now I'm fucked.That's gonna be a pretty big OOF from me, dog.
Hope you can find another, cheap drive.
For the last couple of days I've been browsing PCPartPicker and tried to build something that would work for me, but there's just too many options which makes me crazy. So many choices, and every one of them affects another in some way.
My price range would be around 1000€ and 1300€. I could save some money if I keep my old case and I also have 1Tb SSD which is good enough for me. I also don't give a single shit about how ugly it would look, as long as everything works.
My price range would be around 1000€ and 1300€. I could save some money if I keep my old case and I also have 1Tb SSD which is good enough for me. I also don't give a single shit about how ugly it would look, as long as everything works.

Alright, I found the perfect PC.For the last couple of days I've been browsing PCPartPicker and tried to build something that would work for me, but there's just too many options which makes me crazy. So many choices, and every one of them affects another in some way.
My price range would be around 1000€ and 1300€. I could save some money if I keep my old case and I also have 1Tb SSD which is good enough for me. I also don't give a single shit about how ugly it would look, as long as everything works.

